Problem
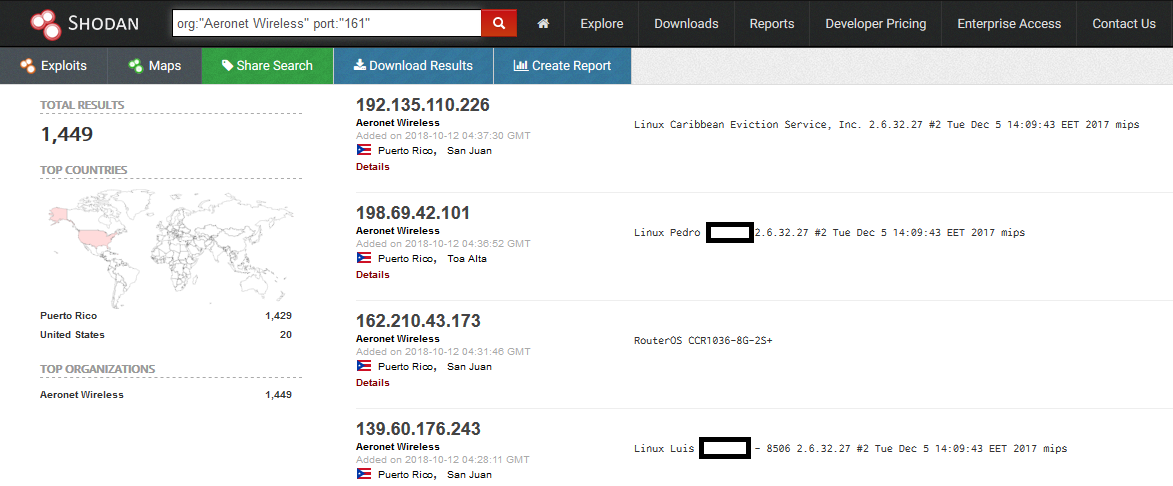
CompSec Direct recently became aware of an information disclosure problem affecting Aeronet Wireless customers in Puerto Rico. In short, querying Shodan.io for Aeronet Wireless and SNMP presents publicly accessible information, such as customer names, IP’s, possible account ID’s and geographic locations.
Why did this happen?
We know ISPs use SNMP to facilitate device management. Adding a customers name (people and companies) into an SNMP field is a stretch and poor consideration of customer privacy.
Are other ISP’s doing the same?
Initial research suggest other ISPs in Puerto Rico, such as OSNET, are also provisioning/configuring customer equipment with customer names in publicly accessible SNMP values. CompSec Direct did not reach out to OSNET as part of this disclosure. In some cases, government offices in Puerto Rico are exposing SNMP entries, but not with personal identifiable information.
At least 1,400 other devices within Puerto Rico have weak/well known SNMP values that facilitate targeted reconnaissance and exploitation.
Why is this dangerous?
For starters, if you are one of the affected customers, anyone can query your name into Shodan.io, get the IP address from presumably your home or office with little effort. Targeted exploitation and “best-effort” geolocation in the records facilitates locations for cyber attacks, stalkers, criminals, private investigators, all now possible thanks to this information; just like the white pages where you could find public telephone numbers.
Geolocation by IP is hardly ever accurate to an exact residence or business address, yet Aeronet Wireless is simplifying the discovery process associated in computer attack campaigns by publishing individual’s information over the web as opposed to business information; which one can argue does not pose the same threat.
Recommended Solution
Aeronet; stop using SNMP this way and block outbound SNMP to WAN. Odd’s are, default or well-known SNMP passwords are also in use.
Are we vulnerable to these kinds of problems?
Call or email us and we will assess your security concerns. Using small pieces of information, we can identify and remediate these kinds of issues to prevent malicious actors from attacking your networks.
Notification timeline
We messaged the Owner of Aeronet Wireless Puerto Rico on Oct 19, 2018. Waited 6 days before publication.
Messaged Aeronet Wireless Owner on Oct 25, 2018 stated that document with disclosure info was not received. Sent Direct Message with disclosure info.
Messaged Aeronet Wireless Owner on Oct, 29, 2018; no response.
Messaged Aeronet Wireless Owner on Oct, 30, 2018 with quick facts; no response.
Messaged Aeronet Wireless Owner on Nov, 9, 2018; no response.
Nov 15 publication due to lack of response from Aeronet Wireless.