The first is actually more common place. The second assumes the admin that maintains WordPress leaves a backup or older version of the file readable by any visitor that happens to “guess” a filename. In the past, CompSec Direct has been successful employing both techniques for customers during security audits, however the second leaves a 404 error easily seen in access logs.
In our case, we used a private dataset and broke it out by countries that use the technique to attempting to access the wp-config.php or renamed wp-config files:
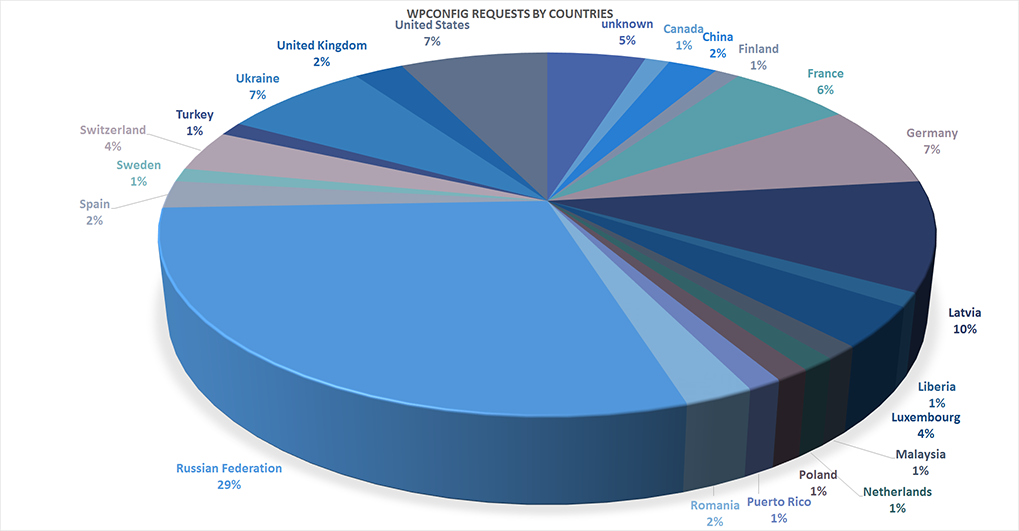
Russia, Ukraine and Latvia take the top 3 countries doing automated scans for wp-config files. In this case, the source ip’s are now dropped since a legitimate user does not try to the wp-config file. If you would like to know how to automate and implement this form of defense, contact our info
[at] compsecdirect.com address in order to schedule some time to explain. In most cases, we can give you a free PoC script to demonstrate the automated defense.