On July 17 2025, we received an email from an IC company. Thing is, we can’t be sure about emails like this since we do Business Development (BD), but none of us knew the person sending the email and the Request For Information or RFI seemed odd.
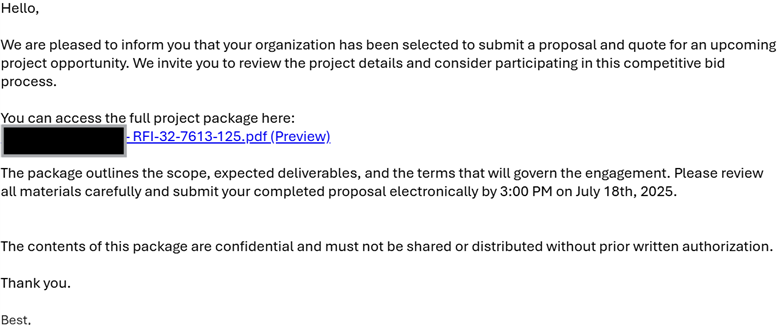
Figure 1: Email with suspicious link: https[:]//siliconoasis.co/connected
Our President, Jose Fernandez, asked a simple question to the person sending the email. This confirmed assumptions.
Figure 2: Simple questions get simple answers.
This is poor tradecraft for three reasons; brevity and lack of explanation, made-up nonsense RFI number and proposal deadline despite being an RFI. Also, you need to execute NDA’s before claiming confidential rights on things like this.
We knew this was a bad attempt at phishing, but the domain checked out, google searching the victim name showed two LI profiles (one very suspicious, and another non-affiliated to the company).
The number on the email, always busy, and eventually routing to an 888 number. BD folks live an die by phones, so the whole setup was bad.
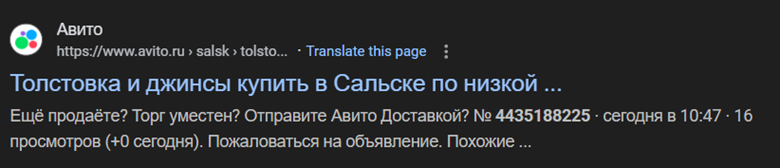
Figure 3: The number shows up on a .ru portal selling clothes?
The number shows up on a post selling clothes, but could be a coincidence.
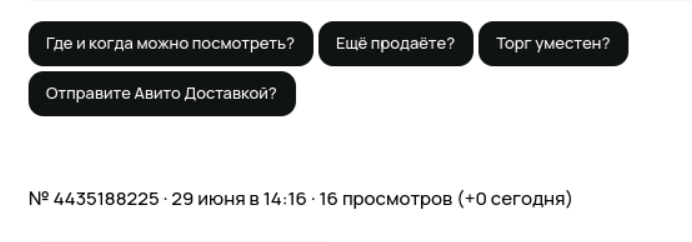
Figure 4: Please answer the phone next time as we are interested in the dress.
Using our Cyber Operations Platform / Cyber Range, Kleared4, to follow the links. If they hijacked the browser; who cares, make a new one. This is why we made this platform.
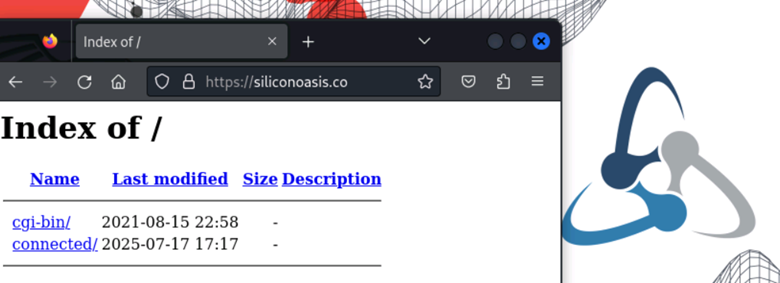
Figure 5: Losing style points here by having directory indexing. cgi-bin was 403
The URL with connected, leads to a fake Bid Application Login.
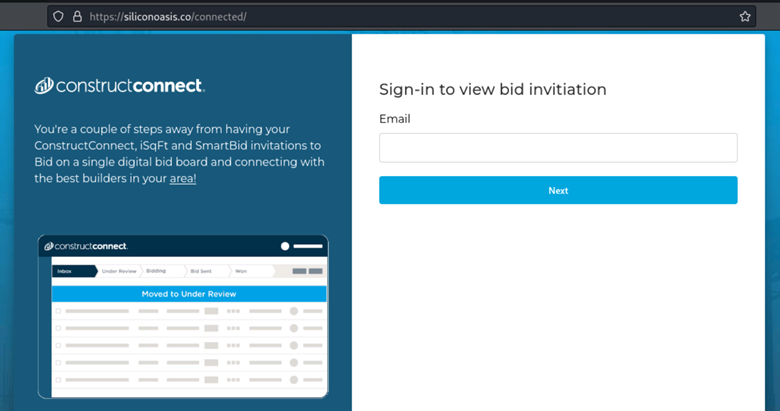
Figure 6: Most BD folks would fall into this as the name is a real product.
Submitting any email, leads to a CloudFlare challenge with data-sitekey=”0x4AAAAAABjCF4cfVVdQxBIT” and data-callback=”” values that change each time.
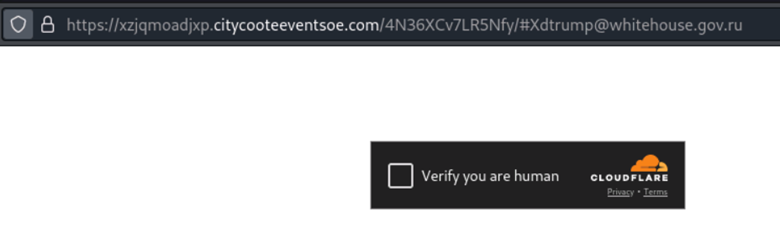
Figure 7: CloudFlare is being used to protect the goods, in this case the page that captures passwords after validating that the email address provided is valid.
IFRAME Data:
<iframe style=”border: medium none; overflow: hidden; width: 300px; height: 65px;” src=”https://challenges.cloudflare.com/cdn-cgi/challenge-platform/h/b/turnstile/if/ov2/av0/rcv/h8wa5/0x4AAAAAABjCF4cfVVdQxBIT/auto/fbE/new/normal/auto/” allow=”cross-origin-isolated; fullscreen; autoplay” sandbox=”allow-same-origin allow-scripts allow-popups” id=”cf-chl-widget-h8wa5″ tabindex=”0″ title=”Widget containing a Cloudflare security challenge”></iframe>
CloudFlare Calls:
https://challenges.cloudflare.com/cdn-cgi/challenge-platform/h/b/turnstile/if/ov2/av0/rcv/tmuno/0x4AAAAAABjCF4cfVVdQxBIT/auto/fbE/new/normal/auto
https://challenges.cloudflare.com/cdn-cgi/challenge-platform/h/b/orchestrate/chl_api/v1?ray=960e34eaa93312c3&lang=auto
https://challenges.cloudflare.com/cdn-cgi/challenge-platform/h/b/flow/ov1/542022581:1752798268:yELBF6ztvnlihKzWtAan3fnILCH2ZgbwGFJ6vbXQyks/960e34eaa93312c3/RHDH3PRGOiM5Ev6AtMB1dWLNGvOhexrP.qtsxmzygKM-1752802152-1.2.1.1-mWzfxCVL.2G5DlDOnckumhqsgHqgaPLLY3f30RspTwNjiZWOSKL3A0snbpHN9vkX
https://challenges.cloudflare.com/cdn-cgi/challenge-platform/h/b/flow/ov1/1604391637:1752798365:lBmLYdE03b0jn8GWm8zARKfiDjflYchgK5AMoAH8y2U/960e3804ce410578/hmuyaq3Tysk9moDop0cut0um0tl68uCHVJw.UoG4Zyg-1752802279-1.2.1.1-rzduZcTNDf8_bjyQOnMZhbDBLaysR8Q8d3oSfJ8sSGL3vYBjR2851sIgn1zUju1s
The domain is a .co, and has privacy protections.
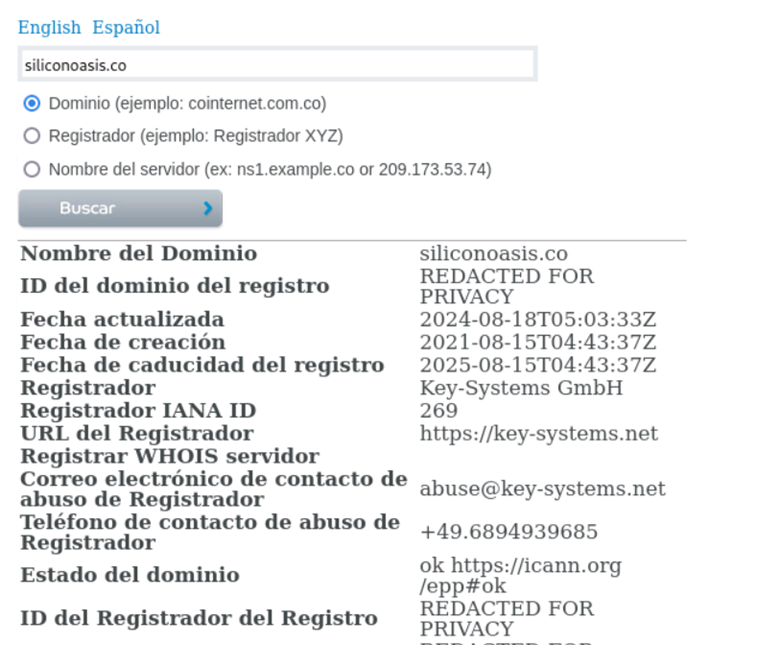
Figure 8: Style Points for using Oasis.
And finally, the fake login page to request your real email and password.
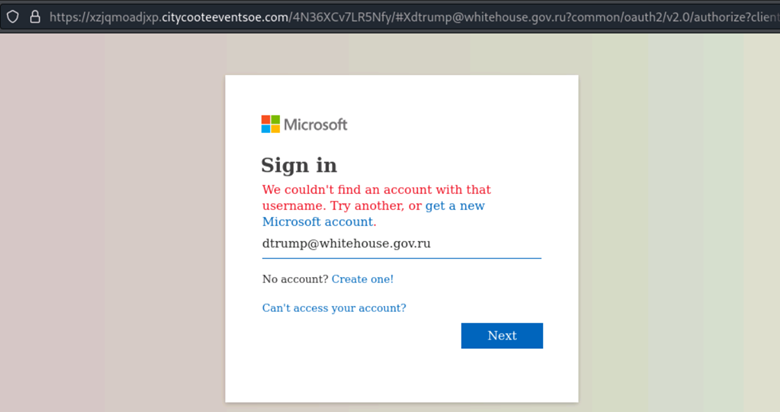
Figure 9: MFA would probably stop this right Jen?
The source code has dumb text, normally found in CN ops to help avoid signatures.
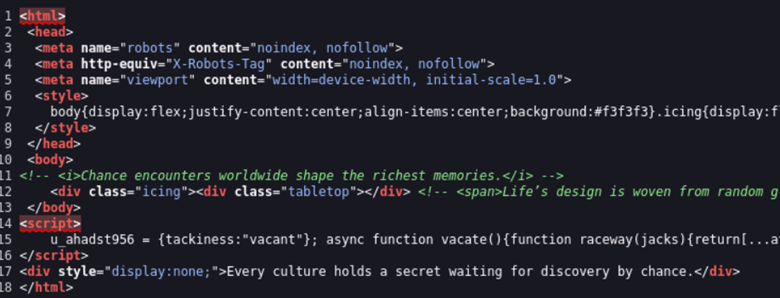
Figure 10: Source code has random quotes, seen in Asian ops.
The page checks for valid accounts, we used a dummy one that is probably around and valid for someone.
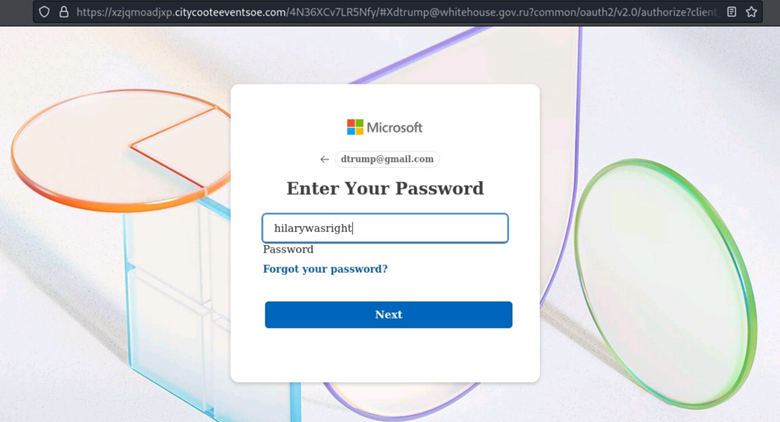
Figure 11: We removed the password field value for laughs, but the app probably redirects correctly.
The last domain, citycooteeventsoe [.]com is questionable.
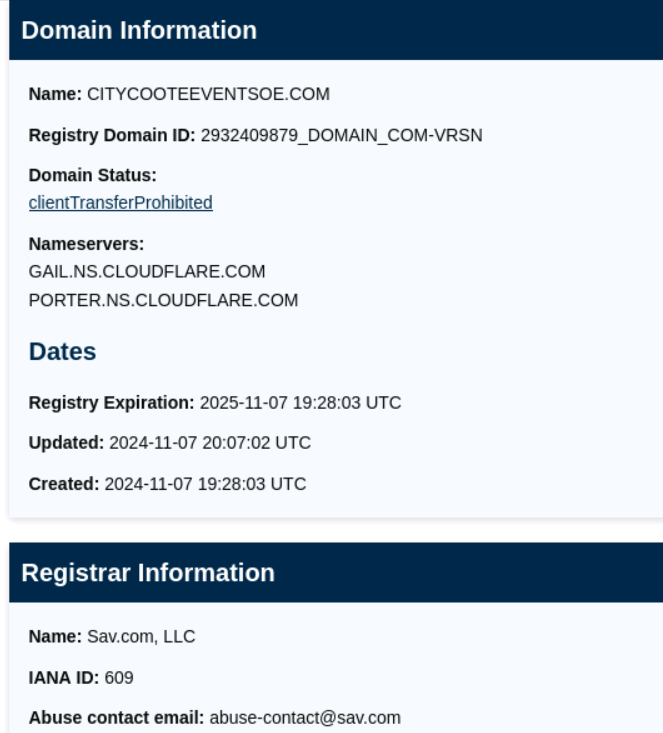
Figure 12: Style points for using domains have both been around for over 6 months.
What can you do when you find these things?
- Let the Business Owner Know; they confirmed BEC.
- Use the abuse contacts and report the domains or IP addresses. Key-Systems 3489874
- Notify CloudFlare.
- Notify Cisa Threat Indicators, 2025-INDICATOR2XU1RG
Why not also notify the FBI or https://www.ic3.gov/ and CISA https://myservices.cisa.gov/irf ?
They require you to establish who the victim was, in this case the BEC victim that sent the emails probably does not want the attention.
Hypothesis: Odds are someone else sent them the phishing email first and this person provided their credentials. no MFA or they accepted the push request.
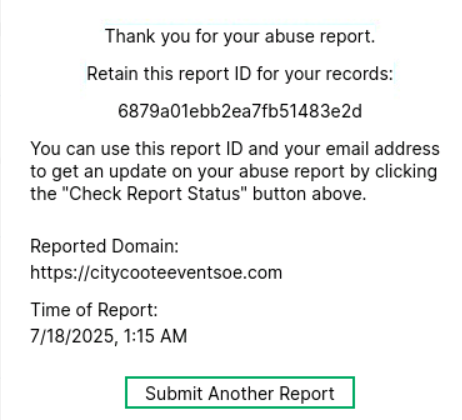
Figure 13: SAV[.]COM abuse complaint.
The IP address of the first domain seems static for now: 199.192.25.75
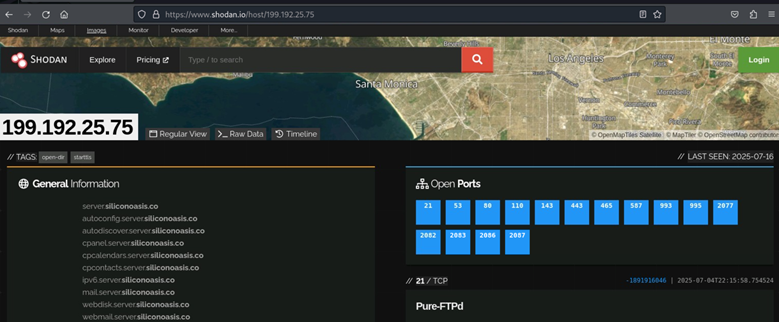
Figure 14:shodan info for siliconoasis[.]co
Second domain is behind a CF load balancer, 172.67.184.195, 104.21.84.17
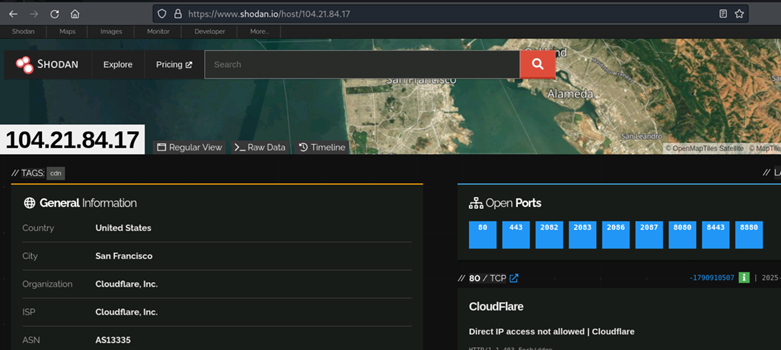
Figure 15: shodan info for citycooteeventsoe[.]com
Figure 16: CF Abuse confirmation
Can we nuke these guys?
Not really, they will change infrastructure and try again soon.
What happens during a BEC?
Everything that person had access to over email and SharePoint, such as proposals, contracts, bids, and contact information from other companies was taken.
What can we do once we detect BEC?
Contact us for Incident Response efforts.
How can we prevent this?
MFA, Block risky sign-ins from non US countries.
Note: Victim info was redacted as time of writing.
Why the bad day?
For us and anyone in this space; making this post, the notifications and getting traction on submissions is similar to hearing the Intro from Doom 2016, but instead of demons its nation states and cyber criminals. Rinse and repeat infrastructure and try again. Till next time; ETP!