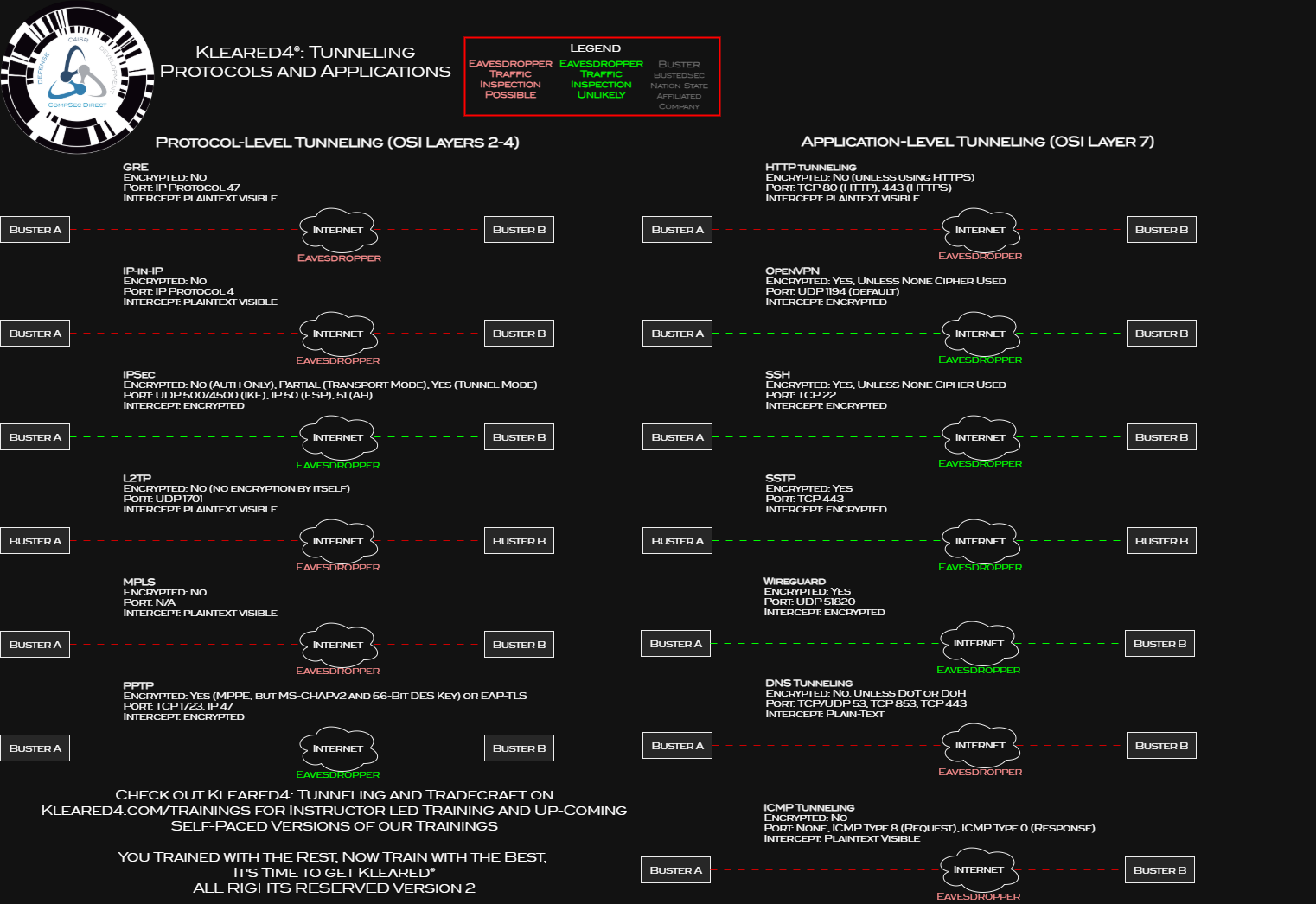
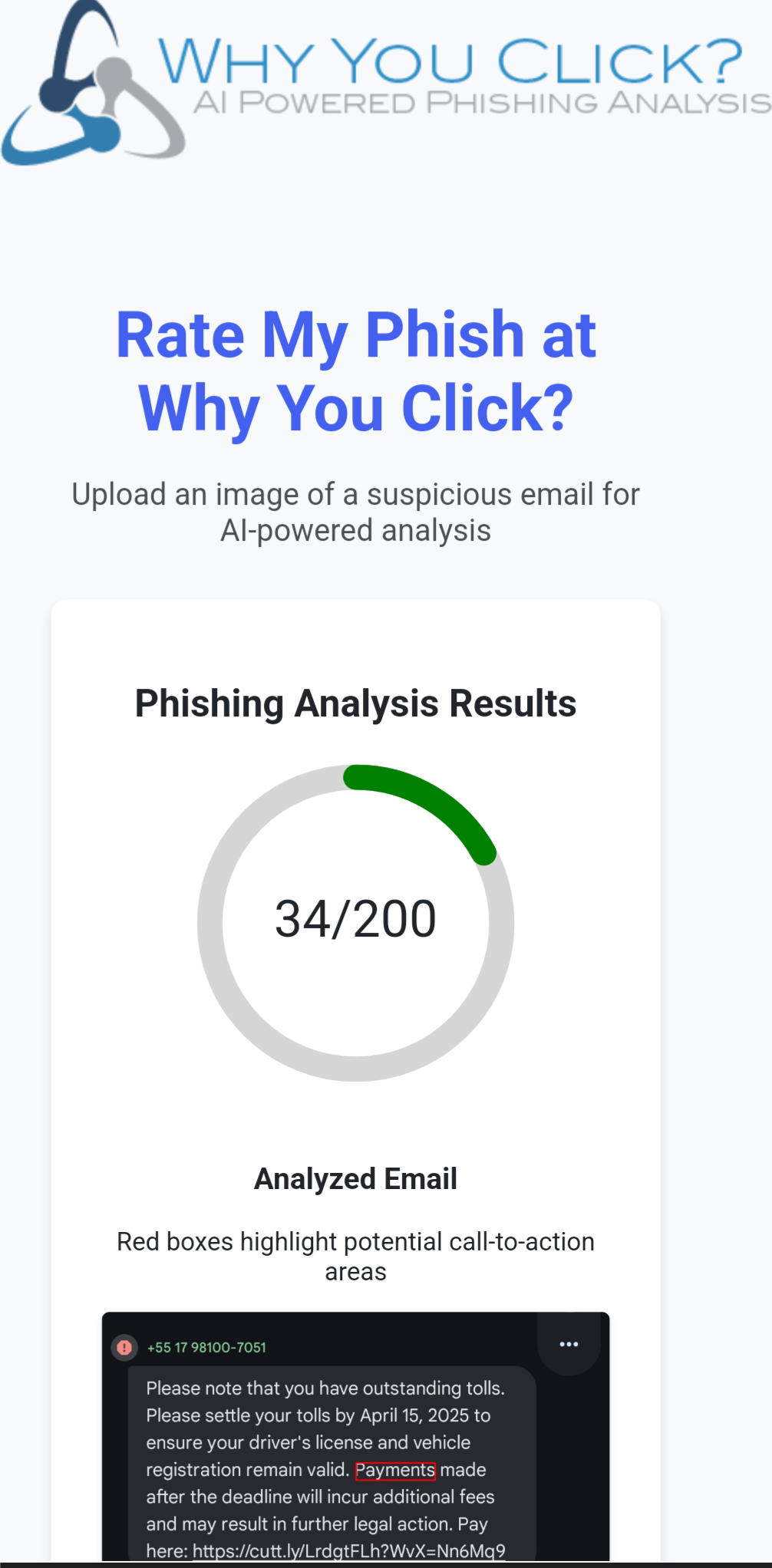
Cyber Range Training on Kleared4
Our class dates for cyber training have been updated for Kleared4: Tunneling and Tradecraft, Kleared4: Incident Responder Windows, Kleared4: Incident Responder Linux, Kleared4: Incident Management and Kleared4: Container Security. All cybersecurity trainings are live, led instructor, and we are making self-paced versions of these courses with our cyber-range Kleared4. All Kleared4 courses include 3 years of [...]