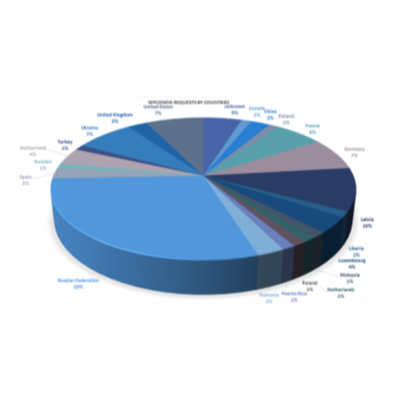
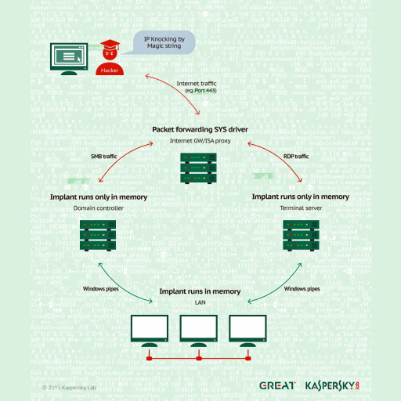
Why going after wp-config is a quick way to get banned
The first is actually more common place. The second assumes the admin that maintains WordPress leaves a backup or older version of the file readable by any visitor that happens to “guess” a filename. In the past, CompSec Direct has been successful employing both techniques for customers during security audits, however the second leaves a 404 [...]