How to exploit Domain Controllers with MS14-068 / From Zero 2 Hero
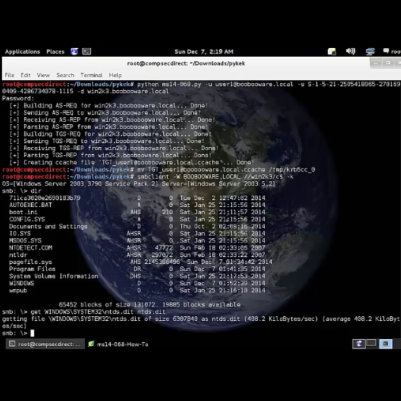
Hello! This is jfer from compsec direct. I would like to show you how to leverage the new Kerberos exploit against Windows domain controllers called ms14-068. This vulnerability allows a user with domain credentials to forge a Kerberos ticket and receive domain admin privileges via the forged ticket. I want to thank Sylvain Monné aka Bidord [...]