Intelligence Community (IC) BEC and Phishing leads to a bad day: Why using Kleared4 kicks ass
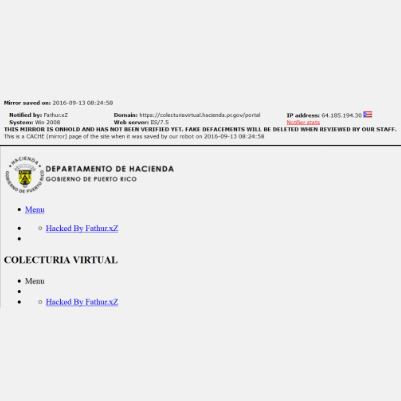
CompSec Direct2025-07-18T13:49:34-04:00On July 17 2025, we received an email from an IC company. Thing is, we can’t be sure about emails like this since we do Business Development (BD), but none of us knew the person sending the email and the Request For Information or RFI seemed odd. Figure 1: Email with suspicious link: https[:]//siliconoasis.co/connected Our President, [...]