Contact us at info[@]compsecdirect.com or via (443)-345-0503
CompSec Direct is a C4ISR firm specialized in Cyber Security. SDVOSB, Buy Maryland Cyber QMCC, & MBE certified company comprised of former network operators from different sectors of the federal government. We are a Maryland CATS+ master contract holder and are looking for new business partnerships to pursue new opportunities.
Use the form below to request additional information about our company and services.
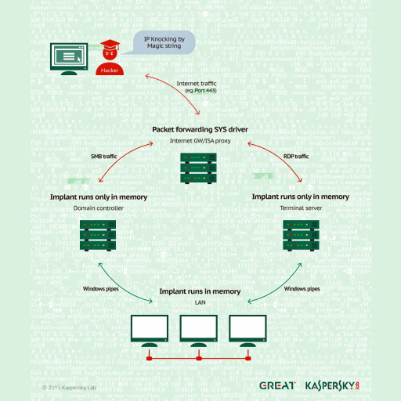
Stepson of Stuxnet stalked Kaspersky for months, tapped Iran nuke talks – ArsTechnica
Excellent report by Kaspersky that unmasks a breach inside their [...]
Bsides PR 2015 – Fun with Tor : How anonymity services complicate actor attribution CompSec Direct
Hello from Puerto Rico. Here are our slides from Jose [...]
BSides Charm 2015 – Mass Hunting and Exploitation with PowerShell Slides CompSec Direct
Hello Everyone, Here are the slides from our presentation at [...]
Pen-testing Guidelines posted from PCI-DSS
PCI-DSS recently released a revised document that covers pen-testing requirements [...]
Cybergeddon: Why the Internet could be the next “failed state” -ArsTechnica
Excellent article by Sean Gallagher from ArsTechnica. It truly captures [...]
11 Signs Someone Is Lying To You – Business Insider
Awesome post from Business Insider’s Vivian Giang. If you are [...]