CompSec Direct recognized by Microsoft with Firmware analysis partner specialization
CompSec Direct is Microsoft approved for firmware analysis. This is a new partner specialization within the Defender for IoT ecosystem of Microsoft's security portfolio. We can help your organization find vulnerabilities within your IoT devices [...]
CompSec Direct is a 2022 VIP Start graduate from the National Veteran Institute For Procurement
We graduated from VIP Start! This is a 4-month program to help small veteran-owned business with government contracting, procurement and growth for small SDVOSB, 8A companies, minority owned companies. If you are a veteran and [...]
CompSec Direct wins firmware analysis prototype event held at Dreamport
After placing 5th on a previous challenge, we were happy to place 1st on a subsequent firmware c. We improved our process, provided analysis and emulation findings to set us apart from the rest. Please [...]
Ransomware case study: echoraix
We are providing our case study on echoraix, a ransomware group that targets network connected storage appliances from QNAP and Synology. Please share this case study with others and contact us for similar case studies, [...]
Trainings @Kleared4
We offer comprehensive cyber security training using our Kleared4 cyber-range. Please use the links below to visit @Kleared4 for class information and details. Please contact us for details on performing in-person training, other options and [...]
Using containers to analyze malware at scale coming to BSides Nova 2023
🕵Our President, Jose Fernandez will run our Using containers to analyze malware at scale (UCTAMAS) workshop at BSidesNoVA on Sep 8, 2023. This is the 4th run of this workshop which takes participant feedback to [...]
My CPAP has a recall; let’s open it instead!
"If you or a loved one has ever used a CPAP device..." Our President, Jose Fernandez, gave a medical device presentation at BioHacking Village during DefCon 31. This presentation focused on bringing awareness to privacy [...]
Know the players in Cyber: how little we know about the leaders of our cyber adversaries
During HammerCon 2022, we ran a timed 60-second 5 question quiz to determine which country was the biggest threat in Cyber. We created adaptive questions sets that would correspond to selections, and we were not [...]
Malware analysis workshop at AvengerCon VII
Our President, Jose Fernandez, ran a malware analysis workshop using containers during AvengerCon VII. The event, hosted at Dreamport in Columbia, MD allowed participants to use Kleared4, our disassociated cyber-range, to safely analyze and triage [...]
Autodyne: Automated firmadyne for firmware emulation
Emulate device firmware using containers with Autodyne. We crossed 2k pulls on dockerhub! Our CI pipeline for daily updated images for ubuntu 18 / ubuntu 20 has been growing strong since we open-sourced the images. [...]
HammerCon 2022 Cyber-Quiz
HammerCon 2022 Cyber-Quiz
BSides Charm 2022
We helped the event by providing sponsorship funds. This allows BSides to continue operating, providing speaking opportunities, and presentation workshops within the local area that would otherwise be presented at larger security conferences. Thanks for [...]
AvengerCon VI
We were exited to sponsor AvengerConVI for a second year.We look forward to the event in 2022. #AvengerCon #CompSecDirect Our T-Shirt was unofficially the winner of best swag. Be sure to checkout local events or [...]
CompSec Direct gets press mentions for cybersecurity expertise
CompSec Direct Executive Team with a a Kleared4 Edge unit. Picture taken by R. Fernandez. We were interviewed in 2021 by El Nuevo Día, a local newspaper in Puerto Rico. Some the of the issues we [...]
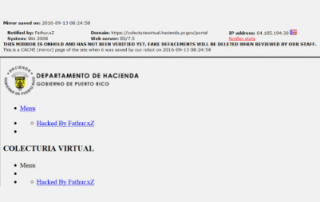
Ransomware: Hacienda of Puerto Rico
Ransomware: Hacienda of Puerto Rico
Kleared4 closed-operation fly-away edge kit
Kleared4 closed-operation fly-away edge kit
Non-attribution classification model published
Non-attribution classification model published
BSides PR 2019
Our President, @jfersec, had the privilege of Keynote during BSides PR 2019. During our presentation, we discussed some hard truth's around: the way DeepFakes and "WeakFakes" are utilizedhow we are good imitators and bad innovators [...]
CTF-Pasteables
“Typing Kills”, so even if you do not agree with this; it’s true. Operator error grows the more you type. It’s akin to “measure twice, cut once”. In Capture the Flags (CTF’s), we often redo [...]
Open-Data wants to be free, but no one looks.
Problem: A few months ago, Giancarlo Gonzales, a former CIO for the island of Puerto Rico, indicated the lack of updates towards open-data in data.pr.gov. As part of an open-data initiative, Puerto Rico created its own [...]
Case 1
Case 1. If you like the case study, hit us up and let us know. Take care. Malware Analysis on Hybrid-Analysis. case1Download
CompSec Direct now approved Cyber-security vendor in Maryland
CompSec Direct has been approved as a Qualified Maryland Cybersecurity Seller (QMCS) by the Department of Commerce of Maryland. This allows us to provide cybersecurity services to qualifying companies under the Buy Maryland Cybersecurity (BMC) [...]
White pages are back!: Aeronet Wireless exposes customer info over SNMP
Problem CompSec Direct recently became aware of an information disclosure problem affecting Aeronet Wireless customers in Puerto Rico. In short, querying Shodan.io for Aeronet Wireless and SNMP presents publicly accessible information, such as customer names, [...]
Data Mining PDF documents; using data conversion to reduce analysis time
Problem A month ago, we became aware of a way to harvest legal notifications from a government web-site. Link Here The web-server allows simple requests to be crafted in order to download PDF documents related to court [...]
Apache brute: A simple brute force deterrent for Linux
We published a simple script to help identify and block possible brute-force attempts on a Linux web-server. The script counts the amount of “bad-actions” an ip has logged in the Apache logs and blocks the [...]
Judicial branch of Puerto Rico exposes sensitive court documents
Problem CompSec Direct recently became aware of an information disclosure problem with the https://unired.ramajudicial.pr/lawyernotificationauthentication/ application used by the judicial branch of the Puerto Rico government. The application uses a weak sequential ID string that is provided to [...]
CompSec Direct’s president presents ZigBee research at local security conference at Inner Harbor
Our President, Jose Fernandez, presented ZigBee research at Bsides Charm 2017 in Baltimore on April 29, 2017. The presentation, called Frony Fronius: Exploring ZigBee signals from SolarCity covered IoT (Internet of Threats) findings on commercial [...]
CompSec Direct receives media mentions as the result from incident response services offered to Hacienda of Puerto Rico
The Center of Investigative News (Centro de Periodismo Investigativo) published an excellent summary of events from the situation the department of Hacienda faced in early March of 2017. Our early involvement in this event helped [...]
CompSec Direct solicited for subject matter expertise on Incident Response for Hacienda of Puerto Rico
CompSec Direct was asked to provide incident response services to the department of Hacienda, the Treasury department of Puerto Rico, on March 7,2017. The department of Hacienda was experiencing daily losses of approximately $20 million [...]
CompSec Direct is awarded CATS+ Master Contract in Maryland
CompSec Direct was awarded a Master contract with the state of Maryland on February, 2017. The CATS+ Master Contract lists provides the state with a list of known vendors in applicable functional areas. We solicited [...]
NTT Group Global Threat Intelligence Report 2016
GTIR 2016 NTT Group published a great threat report for 2016. Quality publication and definitely worth while. Good for CISO’s and Info Sec pros alike. Although some of the areas in the Key Findings are [...]
CompSec Direct’s president presents Shodan research at local security conference in Puerto Rico
CompSec Direct president, Jose Fernandez, presented an open-source intelligence gathering tool called Shodan-Runner at the Bsides PR security conference hosted on Oct 6,2016 in Puerto Rico. The tool allows users to use external CSV files [...]
CompSec Direct hosts remote incident response training for local Puerto Rico students and experts
We hosted a training session on remote incident response operation on Oct 7, 2016. The course was provided “pro-bono” through @Obsidis_NGO, participants paid a small registration fee that covered lunch. Students were able to analyze malware [...]
Forcepoint 2015 Threat Report
An excellent publication from Forcepoint that covers CnC malware, malicious insiders and attribution. Unlike other threat reports, this report covers multiple human factors that are often neglected in technical reports. In some cases, human error and predisposition [...]
Why going after wp-config is a quick way to get banned
The first is actually more common place. The second assumes the admin that maintains WordPress leaves a backup or older version of the file readable by any visitor that happens to “guess” a filename. In [...]
Security firm sued for filing “woefully inadequate” forensics report -Arstechnica
Arstechnica's Dan Goodin has reported that Trustwave is being sued by Affinity Gaming for not eliminating malware presence after a forensic investigation had been done. Mandiant uncovered the malware during a follow up PCI forensic [...]
Wassenaar Arrangement 2013 Plenary Agreements Implementation; Intrusion and Surveillance Items
CompSec Direct and other individuals and companies spoke out against the 2013 Wassenaar Arrangement. We hope our petitions for further revisions are heard. We have included a copy of the document submitted to http://www.regulations.gov/#!docketDetail;D=BIS-2015-0011 Wassenaar Agreement [...]
Stepson of Stuxnet stalked Kaspersky for months, tapped Iran nuke talks – ArsTechnica
Excellent report by Kaspersky that unmasks a breach inside their corporate infrastructure. Stepson of Stuxnet stalked Kaspersky for months, tapped Iran nuke talks
Bsides PR 2015 – Fun with Tor : How anonymity services complicate actor attribution CompSec Direct
Hello from Puerto Rico. Here are our slides from Jose Fernandez’s talk on Tor and attribution. We are very exited to have participated in BSides PR 2015, and look forward to speaking again in the [...]
BSides Charm 2015 – Mass Hunting and Exploitation with PowerShell Slides CompSec Direct
Hello Everyone, Here are the slides from our presentation at Bsides Charm 2015. We look forward to coming back next year for another excellent community driven event.Mass Hunting with Powershell
Pen-testing Guidelines posted from PCI-DSS
PCI-DSS recently released a revised document that covers pen-testing requirements for merchants and security providers. The document does a good job of comparing pen-testing with vulnerability assessments. If your company recently had a pen-test or [...]
Cybergeddon: Why the Internet could be the next “failed state” -ArsTechnica
Excellent article by Sean Gallagher from ArsTechnica. It truly captures the essence of how our world is likely headed into an unfortunate collision with technology. http://arstechnica.com/information-technology/2015/02/fear-in-the-digital-city-why-the-internet-has-never-been-more-dangerous/1/
11 Signs Someone Is Lying To You – Business Insider
Awesome post from Business Insider’s Vivian Giang. If you are into Social Engineering, lying in person is perhaps one of the best ways to accomplish either Corporate Espionage or Penetration Tests. Here are 11 indicators [...]
Subscribing to the DShield Top 20 on a Palo Alto Networks Firewall
This link by Richard Porter provides a quick link to ip’s you can easily blacklist with any iptables or netfilter firewall. Ultimately, it provides a quick list of Tor nodes, known spammers and compromised hosts [...]
How to exploit Domain Controllers with MS14-068 / From Zero 2 Hero
Hello! This is jfer from compsec direct. I would like to show you how to leverage the new Kerberos exploit against Windows domain controllers called ms14-068. This vulnerability allows a user with domain credentials to [...]
CSO – Survey shows the cost of security breaches is on the rise
Excellent post associating the attributed costs of security breaches over time.
Sans- How Not To Fail at a Pen Test
One of the best Sans webinars I have seen in a long time. Thank you Ed and John for putting together such a comprehensive presentation. Read More
IT threat evolution Q2 2014 – Kaspersky
Please take time to read this insightful publication by David Emm, Roman Unuchek, Victor Chebyshev, Maria Garnaeva and Denis Makrushin from Kaspersky Labs. The publication offers unparalleled insight and examples of current evolving threats through [...]
Ransomware going strong, despite takedown of Gameover Zeus – ArsTechnica
Despite numerous public takedowns, cyber criminals will continue to extort users by leveraging their own data as ransom.Click Here for Original Post
Advanced Persistent Threat Awareness Study Results 2014 – ISACA
According to the study by ISACA, 15% of companies are prepared, or feel prepared to handle APT’s. Download Report Here
Dark Reading – How to Defend Your Network from Advanced Persistent Threats (APTs)
Good presentation from Bit9 on using sandboxing to potentially identify APT’s. Click Here
ArsTechnica – How elite hackers (almost) stole the NASDAQ
I recall seeing a NASDAQ trading blackout a few months ago. Although NASDAQ claimed the 4 hour blackout was the result of a high speed trading glitch, it is more probable that these incidents are [...]
ArsTechnica – Millions of dynamic DNS users suffer after Microsoft seizes No-IP domains
Microsoft seized over 22 No IP domains under the pretext that they hosted malicious activity. Is this the cost of being in the security business or have they overstepped legal barriers?
ArsTechnica – We don’t need net neutrality; we need competition
Although I may not agree with current policy regarding net neutrality, this op-ed from ArsTechnica conveys an interesting view point that almost persuades one to move away from net neutrality. Unfortunately, the end of net [...]
DFIR Tournament SANSFIRE 2014
SANS is hosting a forensics challenge this evening that reinforces the need for improved forensic reflexes. For example, if you normally do the same actions when confronted with a task, this becomes a form of [...]
Verizon 2014 data breach report
If you are not familiar with this annual report, please take the time and review the findings from Verizon’s in-depth analysis on data breaches. http://www.verizonenterprise.com/DBIR/2014/reports/rp_Verizon-DBIR-2014_en_xg.pdf
CSD is providing PCI DSS 3.0 vulnerability scanning for clients
PCI DSS 3.0 Changes Recent revisions in PCI DSS 3.0 require that merchants conduct a vulnerability assessment or penetration test against a companies IT resources for the purpose of providing quality assurance for customers. Read [...]